Amazon S3
Amazon S3
Nexla's bi-directional connectors can both send data to and receive data from any data system. This means that once a user has created or gained access to a credential for any data system, building any data flow to ingest data from or send data to a location within that data system requires only a few simple steps.
Authentication
This section provides step-by-step instructions for creating a new Amazon S3 credential that will allow Nexla to authenticate to your Amazon S3 account.
- To create a new Amazon S3 credential, after selecting the data source/destination type, click the Add Credential tile to open the Add New Credential overlay.
New Credential Overlay – Amazon S3
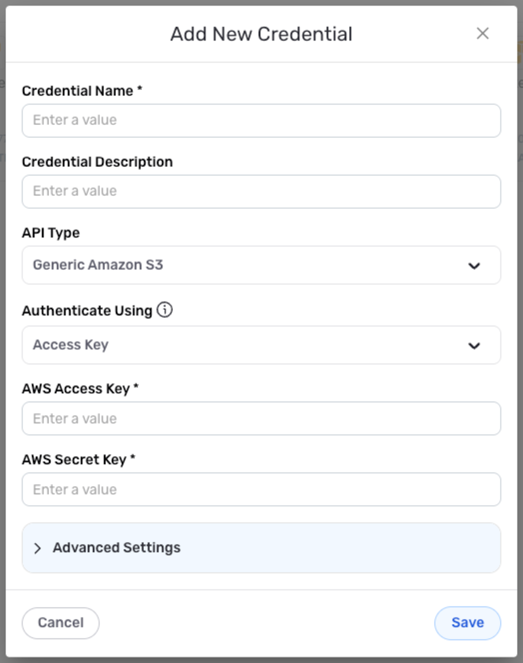
Credential Name & Description
-
Enter a name for the credential in the Credential Name field and a short, meaningful description in the Credential Description field.
Resource DescriptionsResource descriptions should provide information about the resource purpose, data freshness, etc. that can help the owner and other users efficiently understand and utilize the resource.
Authentication Details
-
Select the type of API that this credential will be used to access from the API Type menu.
-
Credentials used to access a Generic Amazon S3 or Odoo ERP Credential API can be configured to authenticate via different AWS permissions mechanisms. Select the authentication method that will be used with this credential from the Authenticate Using menu, and follow the corresponding instructions in the box below to configure associated credential settings.
Configure Authentication Settings
- Access Key
- ARN & External ID
- Instance Role
Authenticate with Amazon S3 using AWS Access and secret keys
- Enter the access key ID that will be used for authentication in the AWS Access Key field. Information about creating and locating your AWS access key is available in AWS IAM documentation.
- Enter the secret access key that will be used for authentication in the AWS Secret Key field.
Authenticate with Amazon S3 using IAM ARN – used to coordinate third-party access to Amazon S3 and other AWS resources
- Enter the external ID assigned for accessing the Amazon S3 account in the External ID field. This is the ID assigned to your user role created by the AWS account owner in the AWS IAM console.
Authenticate using IAM instance role – used to provide temporary access to Amazon S3 and other AWS resources
- No additional settings are required to authenticate using an IAM instance role.
Advanced Settings
For Amazon S3 credentials, advanced settings are available to further refine authentication and file access & handling processes when Nexla accesses the S3 storage location. These settings are optional and can be configured as needed in most cases.
- To access advanced settings for the credential, expand the Advanced Settings section at the bottom of the overlay. Instructions for configuring each available setting are provided in the box below.
Advanced Credential Settings
Amazon S3
- IAM Resource Name
- Restricted Access (S3 Path)
- Client-Side Encryption
- Server-Side Encryption
- File Encryption/ Decryption (Nexla)
The IAM Amazon Resource Name (ARN) is a unique identifier assigned to an AWS resource by the AWS account owner in the AWS IAM console.
If the permissions for this credential are applicable to a specific AWS resource, enter the ARN of the resource in the IAM ARN field.
Enter the ARN in the format
arn:partition:service:region:account:resource.
AWS account owners can grant restricted access to a single S3 bucket or path within a bucket using IAM policies and bucket policies.
If the access permissions for this credential are restricted to a specific S3 bucket or folder path, enter the bucket name or path in the S3 Path List Access is Limited to field.
Enter bucket names in the format
<bucket-name>and folder paths in the format
<bucket-name>/<folder-name>.
Nexla can be configured to encrypt and/or decrypt S3 objects that require client-side encryption using the AWS Key Management System (KMS).
If client-side KMS encryption is applicable for the S3 objects this credential will be used to access:
Check the box next to Enable Client-Side Encryption?, and select the KMS encryption mode that will be used to encrypt/decrypt the S3 objects from the Client-Side Encryption Mode pulldown menu.
Enter the KMS key that will be used to encrypt/decrypt objects in the Amazon KMS Key for Encryption field.
Ensure that the user associated with the KMS key has appropriate KMS permissions to encrypt and decrypt objects.
More information about setting up client-side encryption through AWS KMS and assigning encryption/decryption permissions is available in AWS documentation.
Nexla can be configured to encrypt/decrypt S3 objects that require server-side encryption using either Amazon S3-managed encryption keys (SSE-S3) or AWS Key Management Service (SSE-KMS).
If server-side encryption is applicable for the S3 objects this credential will be used to access:
Check the box next to Enable Server-Side Encryption?.
For server-side encryption performed via AWS SSE-KMS, enter the key ARN in the Key ARN for SSE with KMS field. Leave this field blank for encryption via SSE-S3.
Nexla can be configured to process encrypted files accessed via this credential. The platform will decrypt files before ingestion and encrypt generated files before uploading to the S3 storage location.
To enable file encryption/decryption:
Check the box next to Handle File Encryption/Decryption?, and select the file-encryption protocol that will be used to encrypt/decrypt files from the File Encryption Protocol pulldown menu.
For PGP encryption, enter the following information in the corresponding fields:
External User ID – ID of the user whose public key will be used for encryption/decryption
External User's Public Key – public key that will be used for encryption/decryption
Your User ID for Private Key – user ID that was used to generate the PGP private key
Your Password for Private Key – password for the user ID
Your Private Key – PGP private key that will be used to encrypt/decrypt files
Save the Credential
-
Once all of the relevant steps in the above sections have been completed, click the Save button at the bottom of the overlay to save the configured credential.
-
The newly added credential will now appear in a tile on the Authenticate screen during data source/destination creation and can be selected for use with a new data source or destination.
Data Source
To ingest data from an Amazon S3 location, follow the instructions in the Data Sources section of Common Setup for File-Based Storage Systems.
Data Destination
To send data to an Amazon S3 location, follow the instructions in the Data Destinations section of Common Setup for File-Based Storage Systems.